Remote maintenance solutions
Secure remote access
with KEBA RemoteConnectivity
KEBA RemoteConnectivity is an easy-to-use, high-performing, plug-and-play digital solution for remote machine access through an IEC62443-compliant (CRA-compliant) secure connection, integrated into the Kemro X – KEBA´s platform for industrial automation.
The combination of robust hardware, innovative software, and our reliable servers provide a solid basis for any technological need of machine builders. The offering has the following benefits:
- reduces machine downtime & maintenance costs
- decreases the risk of cyberattacks
- enables a platform for your digitalization services.
Remote maintenance
with KEBA ServiceNet remote support package
KEBA ServiceNet, a support package built on KEBA RemoteConnectivity, is also an integral part of the Kemro X platform.
It integrates easily with OEM applications and has already been incorporated into KePlast application.
The solution has been optimized for temporary access whenever support is needed. In such a case, the solution provides a private network connection, allowing the customer to receive immediate assistance.
Three pillars
of KEBA RemoteConnectivity & their main specifications
SiteManager
- SiteManager is industrial IoT gateway – the access point at the control system, available as a hardware or software solution – secure and IEC62443 certified
- Option 1: SiteManager 15x9 – hardware solution LAN / WIFI / 4G
- Option 2: SiteManager Embedded – Kemro X integrated software solution
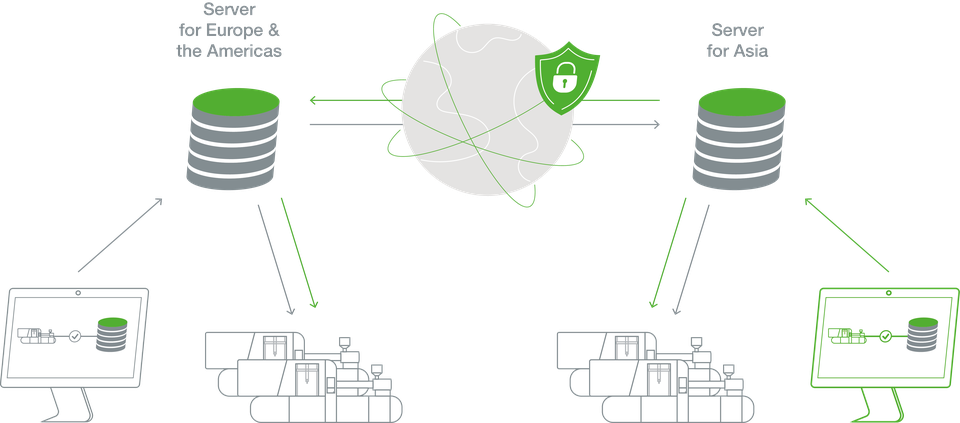
GateManager
- GateManager is the server landscape and the customer management platform for managing customer structures and machines worldwide – manages the connections between SiteManager and LinkManager
- 2 KEBA servers for worldwide coverage (Hong Kong for Asia and in Denmark for Europe & America)
- Manage connections & keep customer‘s infrastructure private
LinkManager
- LinkManager is the PC access point/client software – for the service or engineering team on the OEM or service operator side
- Connect to your customer machine, wherever you are

Security features
of KEBA RemoteConnectivity at a glance
- End-to-end encryption
- Access restricted to specific IP endpoints (and not the entire network)
- Ability to grant access to a specific person to a specific device at a specific time interval
- User authentication compliant with corporate IT policies (integration with active directory, MFA, etc.)
- Two-factor authentication
- Audit trails
- Role-based account management
- Certified according to IEC62443
Current OEM remote maintanance challenges
& your opportunities with KEBA solutions
KEBA ServiceNet provides effective problem-solving solution to reduce machine downtime costs.
We connect your engineers and technical experts with your machine fleet worldwide quickly and at no cost.
Our solution helps you to stay up-to-date with the latest EU security regulations like the EU Cyber Resilience Act (CRA), which prohibits EU-market access to non-complying devices & to keep yourself present in the EU market.
With our user-friendly & turnkey secure access solution, you save yourself time and stay open to possible integration of upcoming KEBA features.
Downloads

Thank you for your request. Our KEBA Customer Support will get in touch with you soon.
Locations
Newsroom

Edge
Chrome
Safari
Firefox